Hybrid Cloud Security: Safeguarding Data in Digital Age

Introduction of Hybrid Cloud Security

In today’s interconnected virtual panorama, hybrid cloud solutions have emerged as a famous desire for organizations seeking flexibility, scalability, and cost performance. However, with this comfort comes the paramount importance of ensuring sturdy security measures to guard sensitive data and hold regulatory compliance. This comprehensive guide delves into the intricacies of hybrid cloud security, exploring key issues, excellent practices, and realistic techniques to guard your precious property.
Understanding Hybrid Cloud Infrastructure
1.1 What is a Hybrid Cloud?
Hybrid cloud security is like having the quality of each world in computing. It blends the ease and scalability of public cloud offerings with the security and manipulation of on-premises infrastructure and personal cloud offerings. It’s a strategic technique that allows companies to combine their IT sources with cloud-based solutions seamlessly. This way, they could experience the flexibility to scale assets while keeping touchy information and critical applications within their controlled environment. In nature, a hybrid cloud offers a pleasant balance between the skill of the cloud & the reliability of traditional infrastructure.
1.2 Key Components of Hybrid Cloud
- On-premises data centers
- Private cloud infrastructure
- Public cloud services (e.g., AWS, Azure, Google Cloud)
1.3 Benefits of Hybrid Cloud
- Scalability
- Flexibility
- Cost-efficiency
- Redundancy
Security Challenges in Hybrid Cloud Environments

Data Privacy and Compliance
Adhering to enterprise regulations like GDPR and HIPAA, even as safeguarding sensitive information across hybrid environments, poses a significant impediment. Organizations ought to navigate complexities to uphold compliance requirements and shield privacy. Balancing the advantages of cloud flexibility with stringent regulatory requirements demands meticulous plans and robust safety features to mitigate risks efficaciously.
Risk of Data Breaches
The decentralized hybrid cloud security structure heightens the potential for unauthorized right of entry, facts breaches, and cyber-attacks. With statistics unfolding throughout multiple environments, there are more excellent access factors for malicious actors to exploit. This necessitates stringent safety features, such as encryption, admission to controls, and non-stop tracking, to mitigate risks successfully and guard sensitive information.
Identity and Access Management (IAM)
Effectively coping with user identities and getting accessory to privileges across diverse clems and on-premises systems needs robust Identity and Access Management (IAM) answers. These solutions ensure that the best legal individuals can access sources, lowering the threat of unauthorized entry or information breaches. Implementing complete IAM strategies includes consumer authentication, role-based get right of entry to control, and continuous monitoring to keep protection across the hybrid surroundings.
Best Practices for Hybrid Cloud Security
Encryption

Implementing stop-to-stop encryption for records in transit and at relaxation is vital for retaining the safety of touchy statistics. This encryption guarantees that even if statistics are intercepted, they stay unreadable and protected from unauthorized admission. By encrypting records at some moment in their journey, businesses can mitigate the threat of reality breaches and safeguard personal records efficiently.
Multi-Factor Authentication (MFA)
Enforcing Multi-Factor Authentication (MFA) provides a coating of security by educating users to deliver several kinds of affirmation in advance rather than having access to help. This consists of something they understand (like a password) and something they have (like a phone, or something they may have (like a fingerprint or facial popularity). MFA significantly enhances security, reducing the likelihood of unauthorized access or breaches.
Regular Security Audits and Assessments
Regular security audits and exams are critical for identifying vulnerabilities and weaknesses in the hybrid cloud security infrastructure. Organizations can directly discover capacity dangers or threats by systematically reviewing protection protocols and configurations and getting access to them. This proactive approach enables timely remediation efforts to strengthen Organization access.
Effective Strategies for Hybrid Cloud Security
Network Segmentation
Using a udA proactive security measure is a ud network in distinct zones with restricted access controls. Organizations can limit the spread of potential security breaches by categorizing the network. This approach ensures that the impact and bolsters are contained if one zone is compromised. Implementing strict access controls within each zone enhances overall network security, minimizing the risk of unauthorized access or data breaches.
Automato swiftly identifies suspicious behavior or potential breaches.
Tools and AI-driven technologies bolster the security posture of hybrid cloud environments. These tools offer real-time threat detection capabilities, continuously monitoring the city to swiftly identify suspicious behavior or potential breaches. Moreover, AI-powered structures can automate incident response, allowing rapid mitigation of security incidents before they increase. By leveraging these modern-day technologies, agencies can shield their hybrid cloud infrastructure against evolving cyber threats.
Disaster Recovery and Backup Solutions
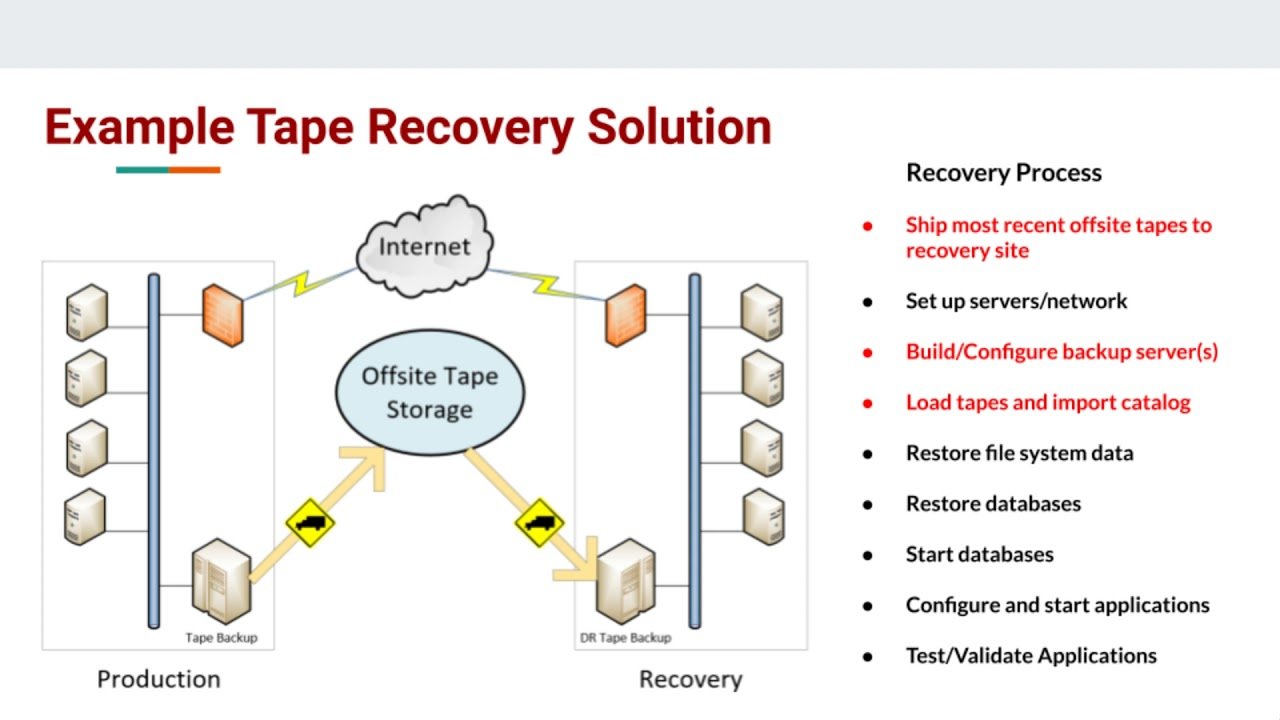
Implementing roto restores operations swiftly in organizations in the event of a disaster in the face of security incidents or system failures. These solutions involve creating redundant copies of criticism by prioritizing disaster recovery preparedness data and establishing contingency plans to restore operations swiftly during a disaster. Organizations can reduce downtime, mitigate financial losses, and uphold customer belief even during challenging circumstances by prioritizing disaster recovery preparedness.
Conclusion
Ultimately, prioritizing hybrid cloud safety is vital in the trendy digital landscape, characterized by typical facts breaches and cyber threats. Understanding the intricacies of hybrid cloud infrastructure and enforcing proactive security measures are critical for groups to successfully mitigate risks, guard touchy information, and uphold regulatory compliance standards. Embracing encryption, multi-component authentication, ordinary security audits, and automated threat detection are pivotal to fortifying a resilient hybrid cloud security posture. By staying vigilant and proactive, companies can navigate the complexities of the hybrid cloud security surroundings while safeguarding their treasured property.
FAQS
How can groups ensure compliance with rules in a hybrid cloud environment?
Businesses ought to enforce vital facts, privacy measures, and encryption and get the right of entry to controls to keep compliance with enterprise guidelines.
What are the common security risks related to hybrid cloud adoption?
Common security risks include information breaches, unauthorized admission, misconfiguration, and lack of visibility across hybrid environments.
How does community segmentation decorate hybrid cloud protection?
Network segmentation divides the hybrid cloud environment into remoted segments, limiting threats' lateral movement and minimizing the impact of capability safety breaches.